The Heidelberg Hybrid Threat Indicator (HTI) builds on the latest methods of empirical social research and applies them to a new combined event dataset (see Data→). This dataset reflects the use of the 33 hybrid instruments identified by Hybrid CoE. Based on these measurement points, complexity; bonding capacity; and deniability are subsequently measured as dimensions of hybrid threats (see Concept→).
The Sequence Network
To determine the complexity of a hybrid threat situation of a specific state, the HTI uses a custom version of sequence network analysis. In this network, the measured instruments are represented as nodes. If the application of two instruments follows one another, they are connected by an edge. In this case, we speak of a combination.
Such combinations can differ based on the time interval between the use of two instruments and the frequency with which these instruments are combined. We use these two distinguishing features to determine how typical a combination is. The more frequent the combination and the smaller the time interval between instruments being used, the greater the “edge weight.”
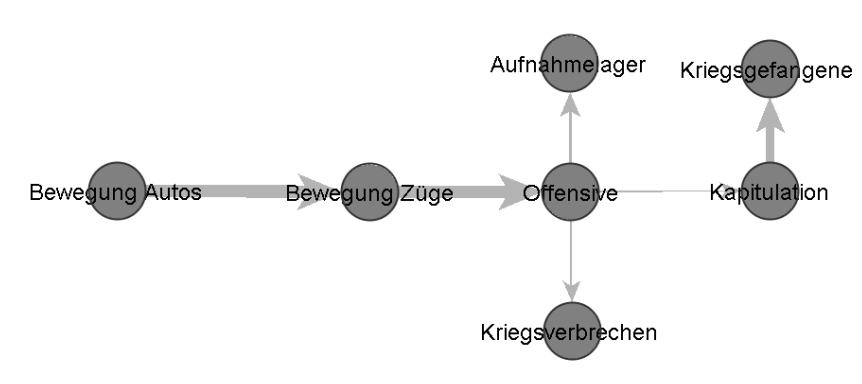
Since the HTI systematically captures some types of instruments (especially cyber incidents) more frequently than others due to its data basis, we subsequently normalise the resulting network along the total frequency of the appearance of individual instruments (but not combinations!).
From Sequence Network to Complexity
How can conclusions about the hybrid threat situation be drawn based on these sequence networks? The HTI methodology assumes that hybrid threats arise from the application of atypical instruments in atypical combinations (see Concept→). The deciding factor is thus the extent to which the measured sequence network for a specific state at a specific point in time is atypical.
First, the HTI determines a typical sequence network as a reference value. This so-called reference graph includes all 30 NATO member states and Ukraine in 2021 and 2022. Specific instrument clusters (or interaction patterns, or situational roles) are identified using the Louvain algorithm.
The reference graph is then compared with the specific network graphs for a specific state at a specific point in time. The hybrid threat situation is thus measured relative to the “typical” situation experienced by NATO states (plus Ukraine).
Typically, similar nodes in a network should lie in the same clusters. This phenomenon is also known as assortativity. The greater the distance of the measured instruments from the typical instrument clusters, the smaller the assortativity; the more atypical the measured instrument clusters, the greater the complexity. According to our calculation, it can range from 0 (= no complexity) to 2 (= full complexity).
The Ambiguity Mixture
In the identified sequence networks, specific instrument clusters can be identified, which the HTI interprets as specific situational roles. This involves the assumption that certain interaction patterns result from specific social constellations. Friends interact in a different way than rivals do, and rivals interact in a different way than enemies do.
In the reference network, we were able to qualitatively identify a total of ten situational roles. These include geopolitical rivals, challengers, participants in armed conflicts, mediators, uncooperative rivals, or hegemons. The ambiguity mixture indicates to what extent these situational roles are pronounced relative to each other at a specific time. To do this, the HTI determines the Jaccard coefficient, which indicates the proportion of measured instruments derived from a specific interaction pattern.
Bonding Capacity
Hybrid threats are often intensified by the establishment of strategic dependencies that can impose costs on a targeted state. The HTI refers to this as “bonding capacity” (see Concept→).
In political science, such dependencies are also referred to as asymmetric interdependences. According to Keohane & Nye (1977), this interdependence creates sensitivity and vulnerability. Sensitivity describes how quickly changes in one country can impose costs on another, as well as how large these costs’ effects are. Vulnerability describes the relative availability and cost of alternatives available to affected states.
Through these two parameters, the HTI can determine bonding capacity. Sensitivity is measured by the trade volume of a state across its borders, while vulnerability is measured by the sum of these sensitivities relative to all trading partners and the unequal distribution of these sensitivities. The latter is determined by multiplying Gini coefficients.
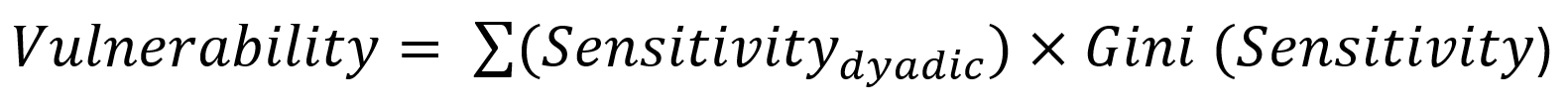
Measure for Ambiguity
The HTI understands the ambiguity of a hybrid threat as a wave moving towards a targeted state. The greater the complexity, the wider the wave, and the harder it is to identify its exact impact vector. The greater the bonding capacity, the higher the wave, and the greater the potential damage a hybrid threat could cause.
Accordingly, the extent of ambiguity can be determined using the formula for calculating an area. It corresponds to the product of complexity and bonding capacity.
Deniability
The deniability of a hybrid attack depends on the nature of the hybrid instrument itself. Generally, it is easier to attribute responsibility for an attack using conventional means to a state than, for example, a cyberattack. The chance of attribution, i.e., assigning responsibility, varies between different hybrid instruments.
In a prototype measurement, we determine deniability based on cyber operations used in a hybrid attack against a state. Using logistic regression, we determine the characteristics of a cyber operation that increase the likelihood of attribution. This method could be extended to other instruments in the future.

